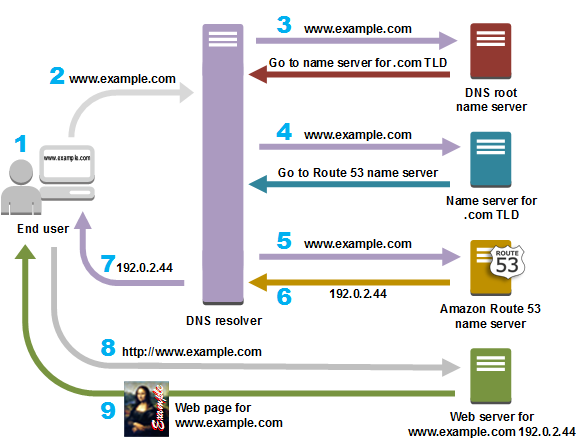
What is a DNS log? DNS logs are records of DNS queries and responses handled by a DNS server. These logs provide detailed information, including the querying device's IP address, the domain name queried, the response provided, and the time of the query.
Where and when to use DNS logs in the industry:
- Security Monitoring: Identify suspicious DNS activity to detect potential malware or unauthorized data exfiltration.
- Troubleshooting: Diagnose issues such as unreachable websites, misconfigured DNS records, or delayed responses.
- Compliance: Maintain logs for regulatory requirements, especially in industries like healthcare or finance.
- Analytics: Understand traffic patterns and optimize DNS configurations.
Practical Example: DNS Logging in AWS
- Create an S3 Bucket for DNS Logs:
- Navigate to the S3 console in AWS.
- Create a bucket (e.g.,
dns-logs-bucket) and enable versioning. - Set appropriate permissions for logging.
- Enable DNS Logging in Route 53:
- Go to Route 53.
- Enable query logging for your public or private hosted zone.
- Select the S3 bucket as the destination for the logs.
- Run
nslookupon an Instance:
- Launch an EC2 instance and SSH into it.
- Run a DNS query, e.g.,
nslookup example.com. - Check the S3 bucket for the log entry related to this query.
DNS Firewall: What It Is and How It Works
What is a DNS firewall? A DNS firewall monitors and filters DNS traffic to prevent users from accessing malicious or unauthorized domains. It uses policies and rules to block queries to known malicious or restricted domains.
Practical Scenario:
- A user cannot access a particular website because the DNS firewall is configured to block it. The DNS firewall works by intercepting DNS queries and blocking them if they match predefined criteria.
How it blocks:
- The block can occur at the DNS resolver level. For example, if an organization blocks access to "malicious.com," any queries for this domain will return an error or a redirection to a warning page.
AWS Route 53 Private Hosted Zones
What is a private hosted zone? A private hosted zone is a DNS zone in Route 53 that is accessible only from specific VPCs. It is used for managing internal DNS records for resources within a private network.
When to use it:
- Internal-only domains: Use it for DNS names that should only resolve within a private network.
- Hybrid cloud setups: Connect on-premises networks to AWS via VPN or Direct Connect.
- Restricted environments: Limit access to sensitive services or applications.
Real-life scenario: An internal company website, internal.example.com, is hosted on a private server accessible only from within the company network. Using a private hosted zone ensures that this DNS record is not publicly resolvable.
Practical Example: Private Hosted Zone
- Create a Private Hosted Zone:
- Go to Route 53 and create a private hosted zone for
example.com. - Associate the hosted zone with a specific VPC.
- Access from an EC2 Instance:
- Launch an EC2 instance in the associated VPC and SSH into it.
- Run
nslookup internal.example.com. If no records are created, you’ll see:
Non-authoritative answer: *** Can't find internal.example.com: No answer
- Create a Record:
- Add a record for
demo.internal.example.comwith an IP like192.192.192.192. - Retry
nslookup demo.internal.example.comfrom the instance. This should now resolve.
- Access from Outside:
- On a local machine, running the same
nslookupwill fail because the record is private:
*** gpon.net can't find demo.internal.example.com: Non-existent domain
Key Point: When creating private zones, ensure they are associated with the correct VPC.
Hybrid DNS and DNS Endpoints
What is hybrid DNS? Hybrid DNS setups integrate on-premises networks with AWS VPCs. This is useful for enterprises with workloads spread across AWS and on-premises systems.
What is a DNS endpoint? A DNS endpoint allows DNS queries between VPCs or between a VPC and on-premises networks.
Practical Setup:
- Scenario: Two instances in different VPCs need to resolve a private domain.
- Instance 1 in VPC1 can resolve
internal.example.comusing a private hosted zone. - Instance 2 in VPC2 cannot resolve it directly.
- Solution:
- Create a Resolver Rule in Route 53 to forward DNS queries from VPC2 to VPC1.
- Ensure security groups and route tables allow traffic.
- Test Resolution:
- From Instance 1:
nslookup internal.example.comresolves successfully. - From Instance 2: Initially fails, but resolves after the endpoint is configured.
Key Takeaways
- DNS Logs: Crucial for security, troubleshooting, and analytics.
- DNS Firewall: Provides an essential security layer for blocking unwanted domains.
- Private Hosted Zone: Use for internal DNS management within specific VPCs.
- Hybrid DNS and Endpoints: Enable seamless DNS resolution across AWS and on-premises setups.
This practical guide shows how DNS-related features in AWS can be used effectively for internal and hybrid network setups, ensuring both functionality and security.